The Duo Blog

One common hurdle for systems administrators setting up new Duo Unix integrations is PAM — Pluggable Authentication Modules.
With PAM, some advance planning will help prevent running into issues later on. That’s because modifying PAM incorrectly can lead to some serious problems, like bypassing Duo altogether or locking users out of their machines.
We hope that the guidance below, combined with our extensive documentation, will help those setting up new integrations get their systems configured quickly and easily.
What is PAM?
PAM stands for Pluggable Authentication Modules. It is used to standardize authentication for Linux systems.
What Does Duo Use PAM For?
Duo makes use of PAM to provide 2FA during login to a Unix system. We integrate with your existing PAM stack configuration, so it’s important that you have a working system before adding Duo.
PAM Basics
-
PAM has a global state that determines whether an authentication will fail or succeed. If the global state is true, then the authentication will pass; otherwise it will fail. This state is determined based on the outcome of the authentication passing through a module.
-
PAM has multiple service modules, such as “auth,” “password,” “account” and “session.” In this context, our concern is the “auth” service module.
-
Each module in the PAM stack will have a different control flag indicating what should happen if the module is passed or failed.
Setting Control Flags
For PAM to function as desired, make sure to properly configure control flags. These come in several different “flavors” that will determine the continuation or failure behavior of a module.
The requisite, sufficient and required flags each lead to different outcomes.
Requisite: If a requisite module passes, then continue down the PAM stack. If a requisite module fails, then set the global state to false and terminate the PAM stack, failing the authentication.
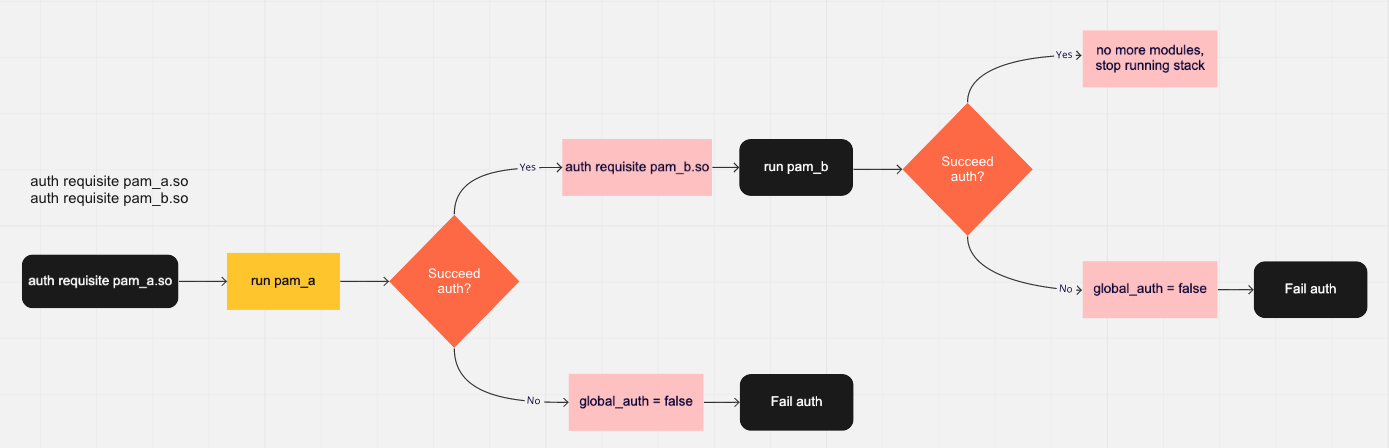
Sufficient: If a sufficient module passes then set the global state to true and return, succeeding the authentication (there are stipulations on this which
[…]
Content was cut in order to protect the source.Please visit the source for the rest of the article.
Read the original article: