While shutting down the technical aspects of malware is critical (see Trickbot on the Ropes Part 1), the real disincentive to the criminals is when you hit them hard in the money. That was the objective of Europol’s Operation 2BaGoldMule case against QQAAZZ. Working with partners in 16 countries, including Latvia, Bulgaria, the United Kingdom, Spain, and Italy, Europol helped to coordinate search warrants being executed at 40 different residences in support of criminal proceedings in the United States, Portugal, and the UK, and Spain.
Europol put out a two-part InfoGraphic as part of their story on the arrests, “20 Arrests in QQAAZZ Multi-Million Money Laundering Case“:
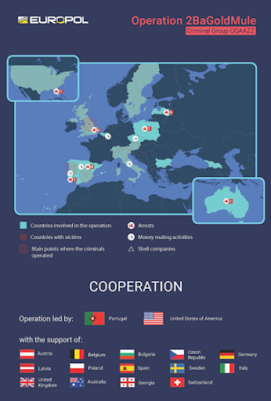

Infographic: https://www.europol.europa.eu/publications-documents/operation-2bagoldmule
The criminals behind the QQAAZZ money laundering ring received funds from botnet operators, and “tumbled” the funds through a variety of shell companies and crypto-currencies to produce “clean money” keeping a 40% to 50% cut of the funds for themselves.
The U.S. Department of Justice says that QQAAZZ-controlled bank accounts received funds stolen via banking trojans including Dridex, Trickbot, and GozNym malware. The DOJ action came in two rounds, with the
first indictment being unsealed back in October 2019 naming these individuals:
Aleksejs Trofimovics
a/k/a Aleksejs Trofimovich, Alexey Trofimovich, Aleko Stoyanov Angelov
Ruslans Nikitenko
a/k/a Krzysztof Wojciech Lewko, Milen Nikolchev Nikolov, Rafal Zimnoch
Arturs Zaharevics
a/k/a Piotr Ginelli, Arkadiusz Szuberski
Deniss Ruseckis
a/k/a Denis Rusetsky, Sevdelin Sevdalinov Atanasov
These individuals used a collection of shell companies to open a large number of bank accounts in Portugal. In 2018, I sat in a meeting in London with a handful of the largest banks in the UK and heard for the first time as they shared information with one another that it was a “common” thing that when someone had their bank account hit by Trickbot, a wire transfer would be sent to Portugal!
According to the indictment, Ruslans Nikitenko used his shell company Selbevulte LDA to open accounts at eleven banks in Portugal. He used the company Colossal Devotion LDA to open accounts at nine additional banks. Arturs Zaharevics created the shell company Cardinal Gradual Real Estate Unipessoal LDA and used it to open accounts at ten banks in Portugal. Dennis Ruseckis created Flamingocloud LDA and used it to open accounts at thirteen banks in Portugal!
According to the October 2019 Indictment, more than $1.1 Million USD in wire attempts were made just for the transactions shown below, although in more than half of the cases, the funds were able to be blocked or recovered.
| Date |
Victim Bank |
Wire Attempt |
Beneficiary |
|
| 07MAR2017 |
Schwab |
$75000 |
Aktrofi Services |
|
| 20SEP2017 |
BOA |
$84900 |
Aktrofi Services |
|
| 26OCT2017 |
JPMorgan Chase |
$98780 |
Privelegioasis |
|
| 29NOV2017 |
American Express |
$121360 |
Selbevulte |
|
| 30NOV2017 |
BB&T |
$72000 |
Privelegioasis |
|
| 08MAR2018 |
USAA |
$29500 |
Flamingocloud |
|
| 08MAR2018 |
USAA |
$29500 |
Colossal Devotion |
|
| 21MAR2018 |
BOA |
$49000 |
Colossal Devotion |
|
| 10APR2018 |
JPMorgan Chase |
$59426 |
Cardinal Gradual |
|
| 10APR2018 |
JPMorgan Chase |
$59426 |
Cardinal Gradual |
|
| 10APR2018 |
JPMorgan Chase |
$59426 |
Cardinal Gradual |
|
| 30AUG2018 |
PNC |
$99693 |
Selbevulte |
|
| 14NOV2018 |
BOA |
$56202 |
Aktrofi Services |
|
| 14NOV2018 |
BOA |
$112921 |
Deinis Gorenko |
|
| 14NOV2018 |
BOA |
$45830 |
Deinis Gorenko |
|
| 06DEC2018 |
JPMorgan Chase |
$114652 |
Flamingocloud |
|
In between that indictment and the current one, there was a bit more publicity back in May 2020 when “
Plinofficial“, a Russian scam-rapper, whose real name was Maksim Boiko, was arrested by the FBI when he landed at the Miami airport, as was covered by the BBC and others at the time.
In the more recent action, the indictment of the US Western District of Pennsylvania was just unsealed, having been filed on 29SEP2020.
This indictment names an additional group of money launderers:
- Nika Nazarovi – of Georgia – aka Nika Utiashvili, Mihail Atanasov, Stefan Trifonov Zhelyazkov
- Martins Ignatjevs – of Latvia – aka Yodan Angelov Stoyanov, Aleksander Tihomirov Yanev, Svetlin Iliyanov Asenov
- Aleksandre Kobiashvili – of Georgia – aka Antonios Nastas, Ognyan Krasimirov Trifonov
- Dmitrijs Kuzminovs – of Latvia – aka Parush Gospodinov
- Valentins Sevecs – of Latvia – aka Marek Jaswilko, Rafal Szczytko
- Dmitrijs Slapins – of Latvia
- Armens Vecels – of Latvia
- Artiom Capacli – of Bulgaria
- Ion Cebanu – of Romania
- TOmass Trescinkas – of Latvia
- Ruslans Sarapovs – of Latvia
- Silvestrs Tamenieks – of Latvia
- Abdelhak Hamdaoui – of Latvia
- Petar Iliev – of Belgium
it says that “in total, cybercriminals attempted to transfer tens of millions of dollars to QQAAZZ-controlled accounts, and QQAAZZ successfully laundered millions of dollars stolen from victims around the world.”
The indictment breaks the criminals into three tiers:
Leaders
Mid-level Managers
and Money Mules
In the September 2020 indictment, some of the victim companies, whose bank accounts were used to wire money to European shell companies created by those named above, included:
- a technology company in Windsor, CT
- an Orthodox Jewish Synagogue in Brooklyn, NY
- a medical device manufacturer in York, Pennsylvania
- an individual in Montclair, NJ
- an architecture firm in Miami, FL
- an individual in Acworth, GA
- an automative parts manufacturer in Livonia, MI
- a homebuilder in Skokie, IL
- an individual in Carollton, TX
- an individual in Villa Park, CA.
Dozens of additional US victims are identified, but it is unknown the total number of victims whose funds were stolen, or attempted to be stolen through these schemes.
Those named in the two indictments received funds to shell company bank accounts including at least 147 accounts opened at banks in Portugal, as well as Germany, Spain, and the United Kingdom.
The indictment provides a partial list of the funds transfers which occurred between US-based victims and accounts controlled by these criminals.
In order to accomplish this, members of the QQAAZZ cash-out system advertised their services on “exclusive, underground, Russian-speaking, online cybercriminal forums.” Some of these advertisements on a single forum cost as much as $10,000 per year!
Some of the online monikers used by QQAAZZ members in these forums included:
qqaazz globalqqaazz markdevido
richrich donaldtrump55 manuel krakadil
kalilinux ritchie totala totala22
These forum exchanges helped to establish relationships between the malware gangs and the money launderers. For example, QQAAZZ members using the name “richrich” chatted with members of the GozNym malware crime group about being a “drop handler” in the UK and Europe and having many accounts that could be used for money laundering, including an account in the name “Yaromu Gida” at a bank in Turkey. That
[…]
Related




