This article has been indexed from The Duo Blog

When’s the last time you finished a project — say, implementing a new cloud integration — without any hiccups or surprises? If you’ve accomplished this recently, congratulations (and please teach me how you did it)! If you haven’t, you’re in good company.
According to Duo’s cloud data provider, our average mid-market customer manages 20 application integrations in their environment. Controlling this access throughout your environment and ensuring the right people get the right access at the right time is incredibly difficult. That’s a key factor in why Gartner’s CARTA model emphasizes how important it is to “continuously discover, monitor, assess, and prioritize risk — proactively and reactively.” So what are we to do in the face of this complexity?
Let’s start with the basics. Your security posture must be designed to serve business access needs within your specific risk context. But business needs and risk environments are constantly changing. Given the changing landscape, you must constantly evaluate and readjust your access policies and posture. That’s where machine learning tools come in, like Trust Monitor, which can identify and flag anomalous events for you to review, providing the context necessary to understand an event’s impact for your unique scenario. From here, you can remediate the event and fine-tune your policy.
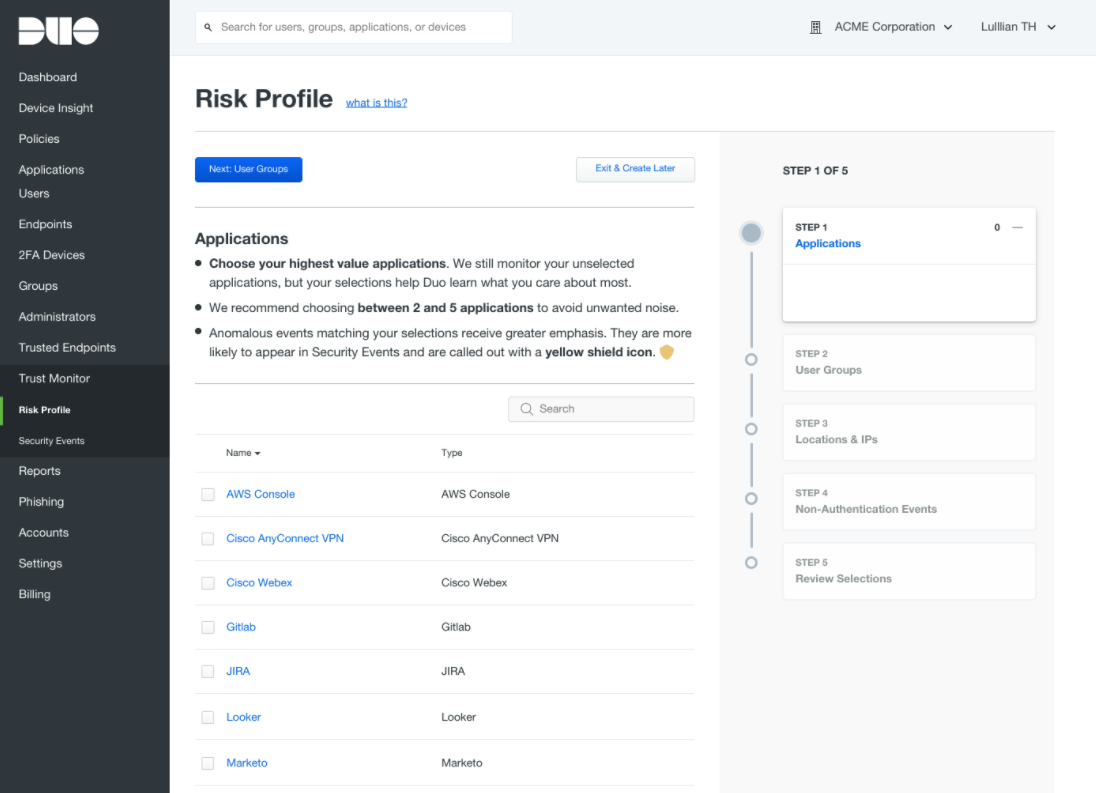
Duo Trust Monitor’s Risk Profile flow enables administrators to select a prioritized set of Duo-protected applications, user groups, and locations/IPs.
Trust Monitor helps you gain visibility by leveraging Duo’s enriched, historical authentication data, shedding light on what’s normal, and what’s atypical, as users and devices access your corporate environment. Understanding anomalous access enables you to harden security posture as well as policy; detect and remediate access risk; and step access requirements up (or down) accordingly. Because it operates on carefully calibrated machine
[…]
Content was cut in order to protect the source.Please visit the source for the rest of the article.
Read the original article: Policy Hardening, and Why Your Security Posture Should Evolve With Your Business Needs