Part 10: Implicit Process Create
Introduction
Welcome back to another installment of the On Detection: Tactical to Functional series. In the previous article, I argued that we perceive actions within our environment at the Operational level (especially when it comes to endpoint events), which means that we should “conceive” of attacker tradecraft at the Operational level as well. In this article, I want to demonstrate WHY this convergence between conception and perception is so important. With that in mind, I want to explore a common issue I see in Detection Engineering (DE); that is, “process based detection.”
In his post describing proposed updates to the data sources represented in MITRE ATT&CK, Jose Luis Rodriguez shared the following graph:
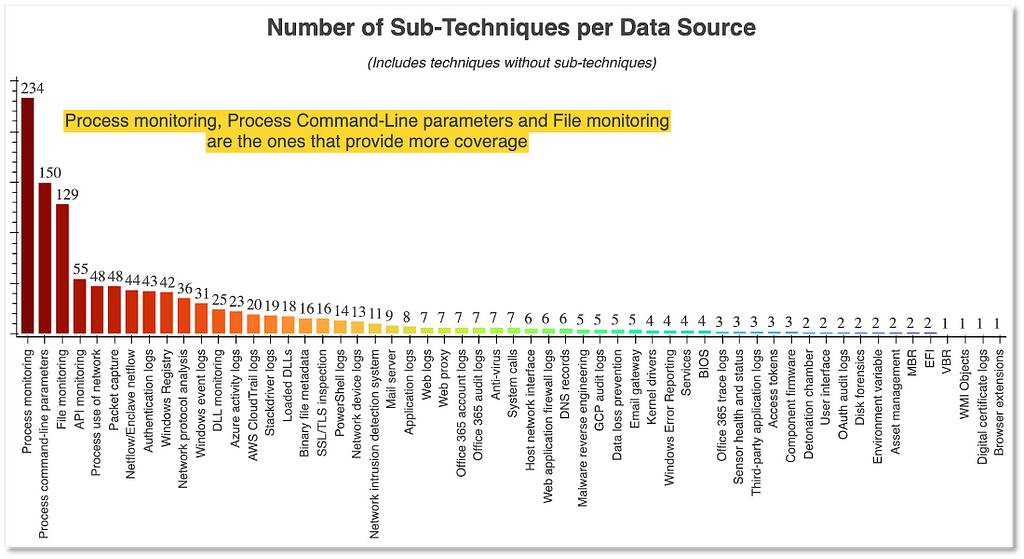
This graph was created based on the relationships between techniques and their associated data sources as they were originally represented in ATT&CK. A quick view of the sheer numbers indicates that “process monitoring” and “process command-line parameters” are far and away the most commonly associated data sources. In fact, “process monitoring” provided coverage of 234 different techniques at the time this graph was produced (i.e., September 2020). So what does this mean for detection engineers? At first glance, one could not be blamed for assuming that if they have process monitoring they have sufficient data to detect the vast majority of techniques. This however is not the case.
According to the MITRE ATT&CK Design and Philosophy white paper a “Data Source” is defined as a, “Source of information collected by a sensor or logging system that may be used to collect information relevant to identifying the action being performed, sequence of actions, or the results of those actions by an adversary. The data source list
[…]
Content was cut in order to protect the source.Please visit the source for the rest of the article.
Read the original article: