This article has been indexed from The Duo Blog

“There are primarily three ways you can authenticate someone: with their username and password, with two-factor authentication, and with a company-supplied device that you can trace. For most stuff, you should have two of those things. For critical things, you should have all three.”
—Alex Stamos, Former Chief Security Officer, Facebook, in WIRED magazine
Adopt a Defense-in-Depth Strategy With Device Trust
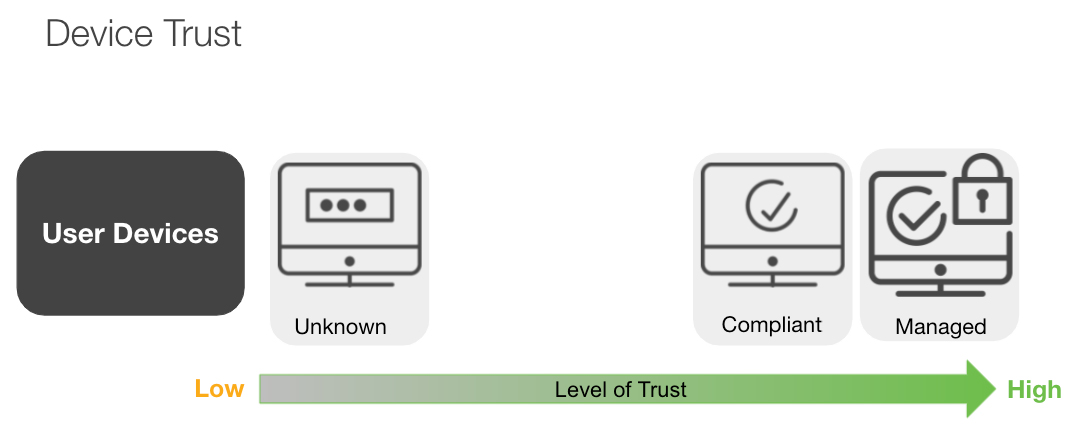
Identifying what devices are accessing corporate applications is critical to understanding the overall security posture of an organization and reducing the risk of unauthorized access.
- Unknown devices offer the lowest level of trust because they’re beyond the control of the IT department.
- Enforcing security requirements such as OS updates and disk encryption help organizations set a baseline for healthy and compliant devices.
- For critical applications and environments with sensitive data (e.g., HIPAA compliance in healthcare or PCI compliance in retail), organizations need to ensure that only managed devices are authorized to access.
Security practitioners are always looking to minimize risk of a data breach, and a common framework to achieve this goal is by leveraging a defense in-depth strategy. Implementing device-based access policies follows this framework by layering on authentication and authorization controls, raising the bar for cyber criminals looking to gain unauthorized access. Even if an attacker compromises an employee’s credentials and somehow manages to get around multi-factor authentication, they would still need to access the application using a compliant and/or managed device.
Establishing Device Trust, Simplified
Since 2017, Duo has enabled organizations to identify if a device is enrolled in the corporate management system and apply device-based access policies based on the management status. Duo administrators may be familiar with the Trusted Endpoints policy, which typically relies on device certificates to verify the management status.
At Duo, we constantly seek feedback from customers to understand their pain
[…]
Content was cut in order to protect the source.Please visit the source for the rest of the article.
Read the original article: Duo Makes Verifying Device Trust as Easy as 1-2-3